1. Start-up
An implementation project is initiated to identify the organisation's requirements, technical design for deployment, covered log sources and specific detection requirements.

Identify cyber threats and ensure compliance
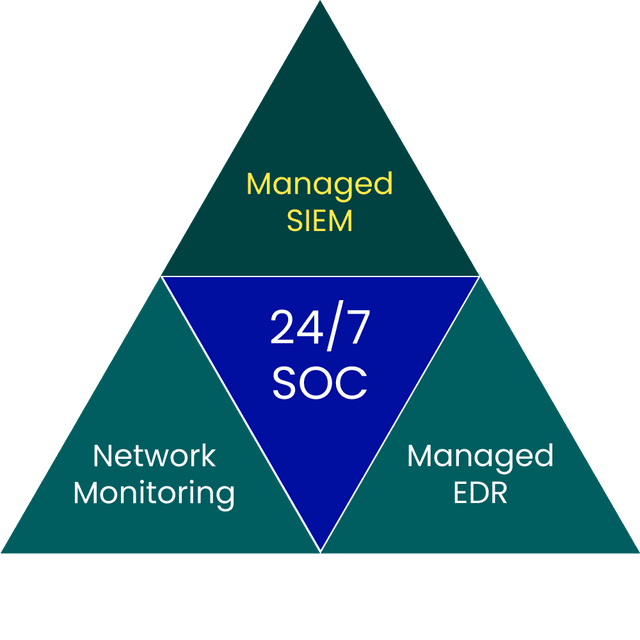
SIEM
BlueSOC Managed SIEM is our fully managed SIEM service, managed by security analysts in Sentor's BlueTeam. By combining market-leading technology, threat intelligence and 24/7 monitoring, we detect and manage threats to your business in near real time. The log data we collect, analyse and deliver will tell you what happened, when it happened, which systems were exposed and which users were involved - essentially all the information you need to manage and report incidents properly.
Contact usWHY SENTOR?
We always follow market developments and use the technology that gives us as MSSP the best capabilities, and you as a customer the most value.
We use a well-established model to identify requirements and relevant logs and to quickly deploy the service. Our completed detection on common log sources also makes it easier to create new use-cases and find relevant events in large volumes of log data.
Our BlueSOC security experts monitor, analyse and manage activity from your logs 24 hours a day, all year round. All alerts are manually validated and enriched by analysts, and incidents are reported and escalated to suit your organisation.
As a customer, you have full access to the standard search interface and can use the relevant log data for other purposes, such as troubleshooting in operations or to create your own dashboards for internal teams.
The service is flexible and can be customised for e.g. proprietary applications, dashboards or detection capabilities specific to your organisation.
You will have a dedicated Service Delivery Manager, who will be responsible for monthly delivery meetings and reporting, and will act as your primary point of contact during ongoing delivery.
the service in brief
An implementation project is initiated to identify the organisation's requirements, technical design for deployment, covered log sources and specific detection requirements.
Changes to the service, such as the addition or removal of log sources, new detection capabilities, etc., are handled on an ongoing basis throughout the service delivery.
We deploy the service in collaboration with you as a customer. To ensure rapid implementation, the project is led by a dedicated Service Delivery Manager from Sentor.
Monthly reporting and regular service meetings with your assigned Service Delivery Manager.
The 24/7 SOC monitoring is activated as soon as the log sources are on-boarded to SIEM and have been approved by quality control. Incidents are escalated as individual tickets in Sentor's customer portal.
We offer several contact routes and provide feedback as soon as possible. If you have sensitive information, we ask you to use the encrypted method.
+46 8 545 333 00
We answer 24/7
info@sentorsecurity.com
For general inquiries
soc@sentor.se
Use our PGP-key