

Endpoint Detection & Response (EDR)
24/7 endpoint detection with active response
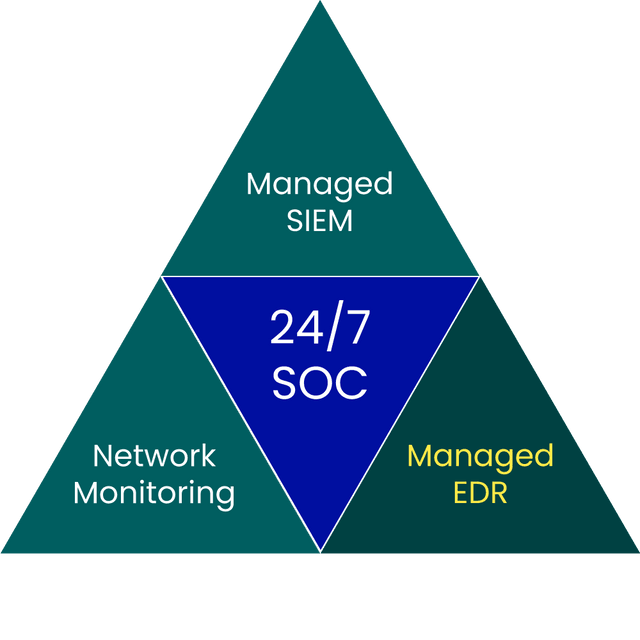
EDR
Users are your business' biggest attack surface
- 68 %
- 68% say that endpoint attacks against their businesses increased between 2018 and 2019
- 8,94
- million USD is the average loss from an endpoint attack
- 80 %
- of successful data breaches are new or unknown "zero day attacks”

Protect your endpoints everywhere, always
The best technology to protect endpoints from attacks is Endpoint Detection & Response (EDR). Our BlueSOC Endpoint Detection & Response service combines leading EDR solutions with Sentor's BlueSOC, staffed by security analysts who monitor and act on suspicious activity around the clock. Our customised solution enables the detection of everything from malware infections, phishing campaigns and access to malicious websites, to advanced APT attacks and anomalous user behaviour. When irregularities are detected, endpoints can be isolated, code blocked and accounts locked, before they escalate into a full-blown incident.
Contact uswhy sentor?
Benefits of EDR from Sentor
the service in brief
How to get started
Workshop
Preliminary workshop to define the scope of the endpoints to be protected, such as clients, servers and operating systems
Delivery begins
Service delivery begins with 24/7 monitoring and analytics from Sentor's BlueSOC
Deployment
Deployment of agents to relevant endpoints and connection to Sentor's SOC
Adaption
Continuous updating of detection functions, whitelisting and functionality for automatic mitigation
Incident plan
An Incident Response Plan (IRP) is developed in collaboration with you and your organisation

Reporting
Monthly reporting and regular service meetings with your assigned Service Delivery Manager
Contact us
We offer several contact routes and provide feedback as soon as possible. If you have sensitive information, we ask you to use the encrypted method.
+46 8 545 333 00
We answer 24/7info@sentorsecurity.com
For general inquiriessoc@sentor.se
Use our PGP-key